After facing a serious cyber attack this year, Executive Director Maree Raftis isn’t pulling any punches with her advice to other education providers.
When General Manager Caspar Zika headed into a VICSEG New Futures’ Melbourne office early one September morning, he wasn’t expecting a very eventful day.
With a quiet office, due to the pandemic, he wasn’t really expecting to see anyone. And he certainly wasn’t expecting to find a big blue message on an executive’s computer screen from a group of hackers called Protect Your System Amigos (PYSA). The message said PYSA had taken down VICSEG’s computer drives by encrypting all their data. To make it worse, that included all their back ups except one.
And so began a flurry of activity that lasted a gruelling six weeks as VICSEG handled the fall out from the cyber attack, which has cost close to $500,000, caused much frustration as staff couldn’t work properly and left an impact on a team already under strain from the pandemic.
VICSEG Executive Director, Maree Raftis, wants to share their story to help other education providers avoid a similar fate.
“It’s the sort of thing you see on TV or hear on the news. You think it can’t happen to you but it can, and it’s been very demanding, distressing and complex” Maree said.
“I really need everyone to know because it can crush you.”
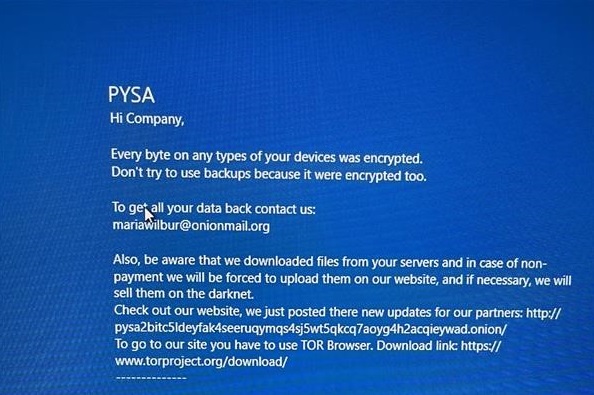
Education providers are prime targets
When it comes to cyber crime, Australia is the fourth most-targeted country in the world and our education sector is particularly popular with cyber criminals (Australian Cyber Security Magazine).
In July this year, our education sector accounted for the most cyber attacks of any sector and reported a 17% increase compared with the first half of the year (Australian Cyber Security Magazine). A common theory is that cyber criminals are capitalising on the security vulnerabilities arising from remote working and learning, including staff and students logging in from personal devices.
Data encryption, otherwise known as ransomware, is one of the most well-known attacks. Others include:
- Infecting devices and networks with viruses
- Phishing to impersonate other people in an attempt to gain access to your system or convince people to pay for fake goods or services
- Data manipulation, to change the outcome of a grade or course
- Data theft, including stealing personal data and selling it on the dark web
Denial of service attacks, which disable web servers by flooding them with requestsThere’s no shortage of articles warning education providers to prioritise cyber security but as Maree says, it’s still one of those things you don’t think will happen to you.
Until it does.

How it went down for VICSEG
When Caspar saw the hackers’ message, he called Maree. At the same time, his IT Manager was calling him after receiving notification that VICSEG’s computer servers had failed overnight, which was originally believed to be an electrical fault.
While the team scrambled to figure out what had happened and what to do next, a meeting was set up with VICSEG’s insurance company. Maree says being insured prevented a bad situation from becoming much worse.
“We were insured for cyber crime, which was a wise decision by an executive years earlier,” Maree said. “Not only because of the money but also because the insurers know how to guide the process and what to do. There’s no way you would know otherwise.”
That process is about as mind boggling as it gets, involving bitcoin, the dark web, forensic IT consultants, lawyers, countless meetings and an overseas firm that specialises in negotiating with hackers in order to retrieve VICSEG’s data.
It was the insurance company that made the tricky decision of whether or not to pay the ransom based on the cost of that versus the estimated cost of recovering the data. But you don’t just pay the ransom and receive your data back.
“There were a series of steps the negotiators had to take,” Maree said. “They had to establish via the dark web that the money was not going to be used for terrorist activities. Then they had to establish if the hackers – known as ‘threat actors’ were ‘ethical and reliable’ – as in, whether they would actually return the data.”
Finally, they agreed on a ransom amount which was paid in bitcoin. More tense days and nights followed until PYSA provided the data encryption tool and VICSEG’s IT team and consultants could begin the process of securely restoring it.
Meanwhile, Maree’s team also had to fulfil obligations to the Office of the Australian Information Commissioner (OAIC) about the potential data breach for all past and present students and staff in their system. Like everything to do with the cyber attack, this was not straightforward and involved a lot of the team’s time and consultants’ expertise, which Maree says has taken a toll.
“They hit you when you’re down. We’re all exhausted from the last few years of the pandemic. We’re now seeing a massive increase in phishing, which we think is just a general increase in cyber crime. Everyone is on tenterhooks.”
Simple steps to protect your business now
Other than insurance, which Maree strongly advises, our Head of Technology Guy De Saram has some simple steps all education providers can take now to safeguard against cyber attacks.
“You don’t need to be a big business to take cyber crime seriously, and you don’t need to be IT savvy,” Guy said. “You just need to know what questions to ask. Cyber security is a journey that even the smallest organisation needs to take.”
One of the most important steps within your control is user behaviour. For a very small price, you can:
- Ensure all your team members use a secure password manager
- Set up two-factor authentication so that team members have to enter a password and code (sent to a different device) to log into your systems and software
These things are often seen as annoying as they slow you down a tiny bit each day, but they make up for it a thousand times by preventing cyber attacks,” Guy said.
Next, ask your IT team or outsourced technology provider some simple questions, such as:
- What is our current cyber security exposure? You can also use this tool from the Australian Cyber Security Centre to assess your current position
- How do we prioritise these risks?
- How do we create a cyber security policy and road map to address these?
- What is our disaster recovery plan?
Those last two points can seem daunting but Guy says they don’t need to be.
“Start with the obvious risk areas and take steps to address them. Starting on the cyber security journey is better than doing nothing.”
You can also engage cyber security specialists to conduct penetration testing on your systems, ideally annually so you know the biggest threats and what to work on. This might not be as affordable for every provider though.
And what do you do if something does happen? If you suspect something, act immediately. For example, if an email looks fishy, alert your team and call your IT support to check it out.
If it’s beyond that and you have been attacked, take it from someone who’s been there like Maree.
“Get your IT to establish what the damage is. And call your insurer straight away – they’ll guide you through the process.”



